The CDI team adopts the DevSecOps culture and practice to provide our customers with quality products. At all phases of the software development lifecycle, security practices are injected to ensure a strong and secure end-product for the customer. During the planning phase, CDI identifies security risks and uncertainties and develops the appropriate mitigation plans for those security risks and uncertainties identified. During the design phase, CDI practices security driven design of the software and all of its corresponding components and their inner workings. During the construction phase, CDI develops and constructs software based on secure designs and utilizes secure programming practices. CDI also leverages third-party security tools such as static code analyzers to ensure a secure product. During the integration phase, CDI will conduct all necessary integration activities required for the software product in a secure fashion. During the verification phase, CDI will construct test procedures which will test all appropriate software requirements with all necessary bounds testing, input/output validation, security testing, etc. During the validation phase, CDI will validate the software security and completeness through formal requirements-based testing by executing tests constructed during the verification phase.
CDI is committed to continuously improving its products. Product Improvement is accomplished by continuous refinement of the DevSecOps four pillars: Organization, Process, Technology, and Governance. Organization improvement can be a result of cultural shift, employee buy-in, communication, collaboration, security, quality assurance, learning from successes, learning from failures, and customer feedback. Process improvement can be a result of collaborative design, test-driven development, command and automated tasks, continuous adaption and improvement, and continuous authority to operate. Technology improvement can be a result of tool adaption, automation and orchestration, cloud and containerization, infrastructure as code, and security as code. Governance improvement can be a result of built-in governance control, uniform policy enforcement, data-driven validation, enhanced visibility, and inherited certifications and authorizations.
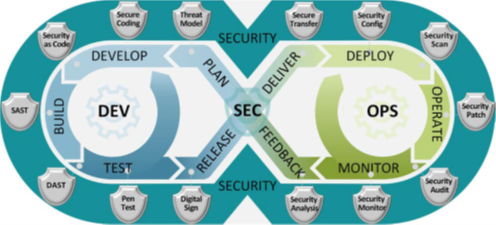
What is DevSecOps?
DevSecOps is an organizational software engineering culture and practice that aims at unifying software development (Dev), security (Sec), and operations (Ops). The main characteristic of DevSecOps is to improve customer outcomes and mission value by automating, monitoring, and applying security at all phases of the software lifecycle: plan, develop, build, test, release, deliver, deploy, operate, and monitor. Practicing DevSecOps provides demonstrable quality and security improvements over the traditional software lifecycle, which can be measured with these metrics:
- Mean-time to production: the average time it takes from when new software features are required until they are running in production.
- Average lead-time: how long it takes for a new requirement to be delivered and deployed.
- Deployment speed: how fast a new version of the application can be deployed into production environment.
- Deployment frequency: how often a new release can be deployed into the production environment.
- Production failure rate: how often software fails during production.
- Mean-time to recovery: how long it takes applications in the production stage to recover from failure.
In addition, DevSecOps practice enables:
- Fully automated risk characterization, monitoring, and mitigation across the application lifecycle.
- Software updates and patching at a pace that allows the addressing of security vulnerabilities and code weaknesses.
DevSecOps practice enables application security, secure deployment, and secure operations in close alignment with mission objectives. In DevSecOps, testing and security are shifted to the left through automated unit, functional, integration, and security testing, which is a key DevSecOps differentiator since security and functional capabilities are tested and built simultaneously. In addition, some security features are automatically injected into the application without developer intervention via a sidecar container.